
A 24-year-old Australian man has been charged for his alleged role in the creation and sale of spyware for use by perpetrators of domestic violence and child sex offenders.
Jacob Wayne John Keen, who currently resides in Frankston, Melbourne, is said to have created the remote access trojan (RAT) when he was 15 years old, while also administering the tool from 2013 until it was shut down in 2019 as part of a coordination led by Europol. exercise.
“The Frankston man engaged in a ring of individuals and sold spyware, called Close monitor (IM), to more than 14,500 individuals in 128 countries,” the Australian Federal Police (AFP) claimed in a press release over the weekend.

The defendant is charged with six counts of committing a computer offense by developing and supplying malware, in addition to profiting from its illegal sale.
Another woman, 42, who lives in the same house as the accused and identified as his mother by The Guardian, has also been charged with “handling the proceeds of crime”.
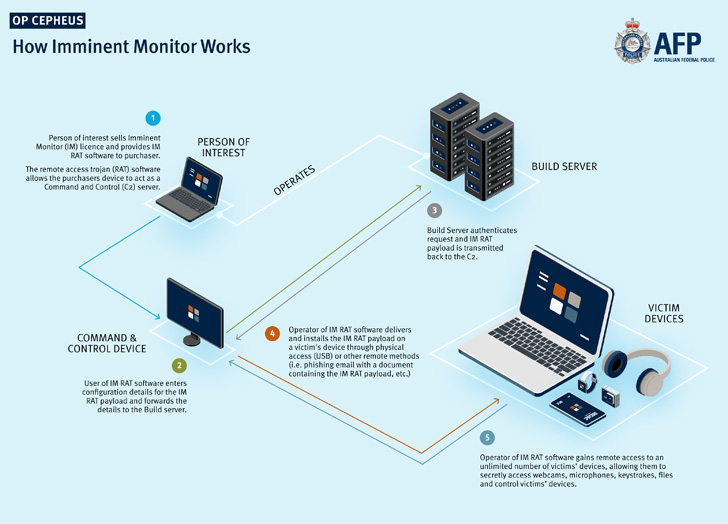
AFP said the investigation, codenamed Cepheus, was set in motion in 2017 when it received information about a “suspicious RAT” from cybersecurity firm Palo Alto Networks and the US Federal Bureau of Investigation (FBI).
The operation, which saw 85 search warrants executed globally in cooperation with more than a dozen European law enforcement agencies, culminated in the seizure of 434 devices and the arrest of 13 people for using the malware for malicious purposes.
No fewer than 201 individuals received RAT in Australia alone, with 14.2% of purchasers named as respondents to domestic violence orders. Also among the buyers is a person registered on the Child Sex Offender Registry.

Distributed via email and text messages, Imminent Monitor came with the ability to covertly record keystrokes, as well as record webcams and device microphones, making it an effective tool for users to keep tabs in their targets.
Later versions of the Windows malware also introduced options for “hidden” Remote Desktop Protocol (RDP) access and even running a cryptocurrency miner on victim machines – a feature not usually associated with a remote access tool .
The surveillance equipment, sold for around $35 AUD on an underground hacking forum, is estimated to have earned the operator somewhere between $300,000 and $400,000, most of which was then spent on food delivery services and other consumables and available, AFP said.
According to a 2019 report from Unit 42, John Keene went by the alias “Shockwave™” and had previously offered a distributed denial-of-service (DDoS) tool called Shockwave™Booter in early 2012, before passing in Imminent Monitor.

The agency said it believed there were tens of thousands of victims worldwide, including 44 in Australia. If convicted, the suspect faces a maximum sentence of 20 years in prison.
“These types of malware are so insidious because they can give an offender virtual access to a victim’s bedroom or home without their knowledge,” said Chris Goldsmid, AFP cyber crime operations commander.
“Unfortunately there are criminals who not only use these tools to steal personal information for financial gain, but also for very intrusive and heinous crimes.”



