
A month-long cyber espionage campaign undertaken by a Chinese nation-state group targeted several entities with detection malware in order to gather information about its victims and fulfill its strategic goals.
“The targets of this latest campaign include Australia, Malaysia and Europe, as well as entities operating in the South China Sea,” enterprise security firm Proofpoint said in a release in partnership with PwC.
Targets include Australian local and federal government agencies, Australian news media companies and global heavy industry manufacturers carrying out fleet maintenance of wind turbines in the South China Sea.
Proofpoint and PwC attributed the intrusions with moderate confidence to a threat actor tracked by the two companies named TA423 and Red Ladon respectively, which is also known as APT40 and Leviathan.
APT40 is the name given to a China-based, espionage-motivated threat actor known to be active since 2013 and has a pattern of striking entities in the Asia-Pacific region, with a primary focus on the South China Sea . In July 2021, the US government and its allies linked the adversary collective to China’s Ministry of State Security (MSS).

The attacks took the form of several phishing campaign waves between April 12 and June 15 that used URLs masquerading as Australian media firms to deliver the ScanBox detection framework. The phishing emails came with subject lines such as “Sick Leave”, “User Request” and “Request Cooperation”.
Unlike watering holes or strategic web compromises where a legitimate website known to be visited by targets is infected with malicious JavaScript code, APT40 activity uses an actor-controlled domain used to deliver malware.
“The threat actor often posed as an employee of the fictitious media publication ‘Australian Morning News’, providing a URL to the malicious domain and asking targets to view its website or share research content that the site the Internet would publish,” the researchers said.
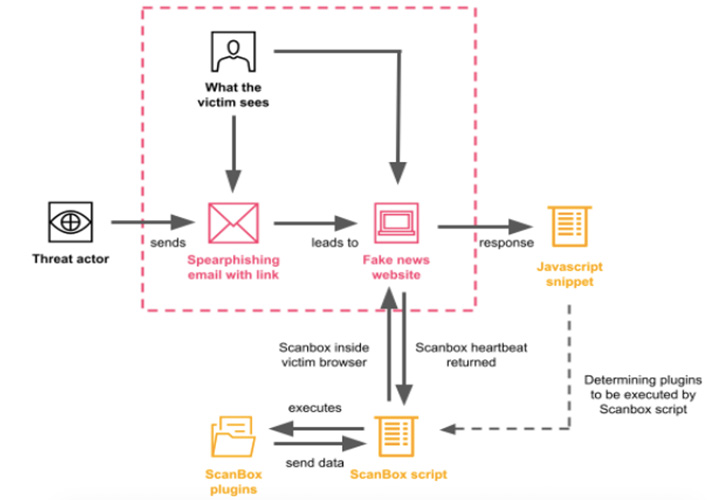
ScanBox, used in attacks as far back as 2014, is a JavaScript-based malware that enables threat actors to profile their victims as well as send next-stage payloads to targets of interest. It is also known to be privately shared among several China-based hacker groups, as are HUI Loader, PlugX, and ShadowPad.
Some of the notable threat actors that have been previously observed using ScanBox include APT10 (aka Red Apollo or Stone Panda), APT27 (aka Emissary Panda, Lucky Mouse or Red Phoenix) and TA413 (aka Lucky Cat).
Also picked up and executed by the malware on the victim’s web browser are a number of plug-ins that allow it to record keystrokes, fingerprint the browser, collect a list of installed browser extensions, communicate with infected machines and check the presence of Kaspersky Internet Security Software (KIS).

This is not the first time that APT40 has adopted the modus operandi of using fake news websites to deploy ScanBox. A 2018 phishing campaign discovered by Mandiant used news article URLs hosted on a fraudulent domain as lures to trick recipients into downloading malware.
Interestingly, the April-June attacks are part of sustained phishing activity linked to the same threat actor targeting organizations based in Malaysia and Australia, as well as global companies that may be linked to offshore energy projects in South China Sea from March 2021 to March 2022.
These attacks used malicious RTF documents to deliver a first-stage downloader that then acted as a conduit to obtain encrypted versions of the Meterpreter shellcode. One of the victims of this campaign in March 2022 was a European manufacturer of heavy equipment used in offshore wind farms in the Taiwan Strait.
That’s not all. APT40 has also been attributed as being behind Copy-Paste Compromises the Australian Cyber Security Center (ACSC) discovered in June 2020, which were directed against government agencies.
“This threat actor has demonstrated a sustained focus on entities involved in energy exploration in the South China Sea, along with domestic Australian targets including defense and healthcare,” the researchers said.



