
About three different but related campaigns between March and June 2022 have been found to deliver a variety of malware, including ModernLoader, RedLine Stealer, and cryptocurrency miners to compromised systems.
“Actors use PowerShell, .NET assemblies, and HTA and VBS files to spread to a target network, eventually dropping other pieces of malware, such as the SystemBC trojan and DCRat, to enable various stages of the operation. them,” Cisco researcher Talos Vanja. Svajcer said in a report shared with The Hacker News.

The malicious implant in question, ModernLoaderis designed to give attackers remote control over the victim’s machine, which allows adversaries to install additional malware, steal sensitive information, or even capture the computer in a botnet.
Cisco Talos attributed the infections to a previously undocumented but Russian-speaking threat actor, citing the use of off-the-shelf tools. Potential targets included Eastern European users in Bulgaria, Poland, Hungary and Russia.
The infection chains discovered by the cybersecurity firm include attempts to compromise vulnerable web applications such as WordPress and CPanel to distribute malware via files masquerading as fake Amazon gift cards.
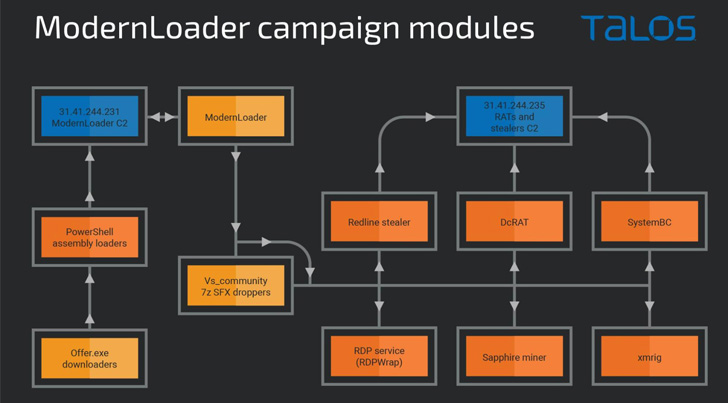
The first-stage payload is an HTML application (HTA) file that executes a PowerShell script located on the command and control server (C2) to initiate the deployment of intermediate payloads that ultimately inject malware using a technique called emptying the process.
Described as a simple .NET remote access trojan, ModernLoader (aka Avatar bot) is equipped with features to collect system information, execute arbitrary commands, or download and execute a file from the C2 server, allowed the opponent to change the modules in real time.

Cisco’s investigation also uncovered two earlier campaigns in March 2022 with similar modes of operation that use ModerLoader as the primary C2 malware communications and serve additional malware, including XMRig, RedLine Stealer, SystemBC, DCRat, and a Discord token stealer, among others. others.
“These campaigns portray an actor experimenting with different technologies,” Svajcer said. “Using off-the-shelf tools indicates that the actor understands the TTPs required for a successful malware campaign, but their technical skills are not developed enough to fully develop their tools.”



