Based on the findings of the 2022 Malwarebytes Threat Review, 40 million Windows business PC threats were detected in 2021. To combat and avoid these types of attacks, malware analysis is essential. In this article, we’ll break down the purpose of malware investigation and how to perform malware analysis with a sandbox.
What is malware analysis?
Malware analysis is a process of studying a malicious sample. During the study, a researcher’s goal is to understand the type, functions, code and potential dangers of a malicious program. Get the information the organization needs to respond to the intervention.
Analysis results you get:
- how the malware works: if you investigate the program’s code and its algorithm, you will be able to stop it from infecting the entire system.
- program features: improve detection using malware data such as family, type, version, etc.
- what is the purpose of the malware: enable the sample run to see what data is targeted, but of course, do it in a safe environment.
- who is behind the attack: get the IPs, origins, TTPs used and other traces that hackers hide.
- a plan on how to prevent this type of attack.
Types of malware analysis
 |
| Static and dynamic analysis of malware |
The main steps of malware analysis
In these five steps, the main focus of the investigation is to find out as much as possible about the malicious sample, the execution algorithm and how the malware works in different scenarios.
We believe that the most effective method to analyze malware is a mix of static and dynamic methods. Here is a short guide on how to do malware analysis. Just follow the steps below:
Step 1. Set up your virtual machine
You can customize a VM with specific requirements such as browser, Microsoft Office, select OS bit and location. Add analysis tools and install them on your VM: FakeNet, MITM proxy, Tor, VPN. But we can easily do it in ANY.RUN sandbox.
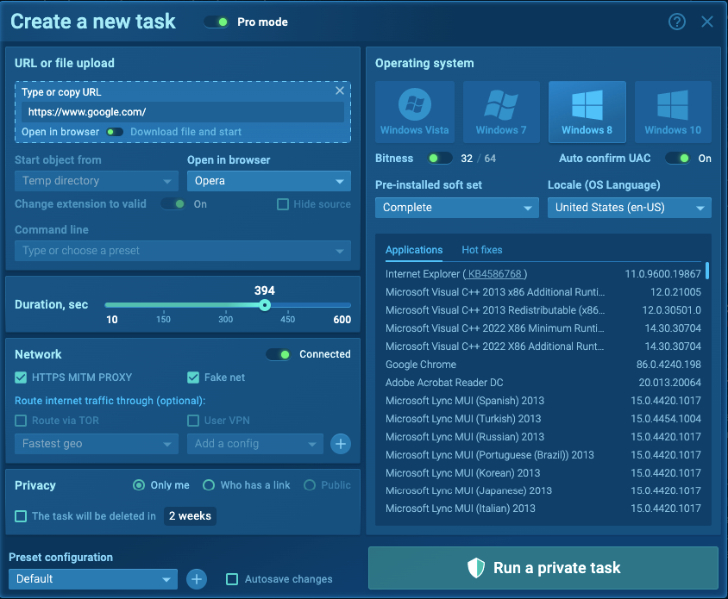 |
| VM customization in ANY.RUN |
Step 2. Review the static properties
This is a stage for static malware analysis. Examine the executable file without running it: check the strings to understand the functionality of the malware. The hashes, strings, and content of the headers will provide an overview of the malware’s intentions.
For example, in the screenshot below, we can see the hashes, PE Header, mime type and other information of the Formbook sample. To get a brief idea about the functionality, we can take a look at the Import section in a sample malware analysis, where all imported DLLs are listed.
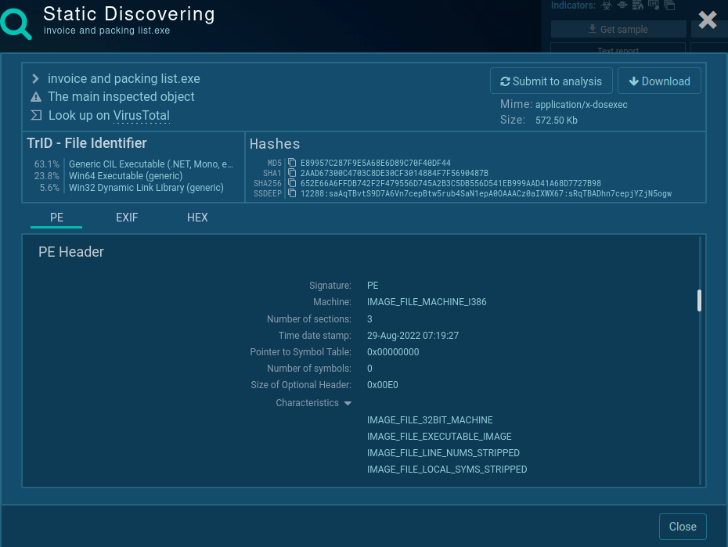 |
| Static detection of PE file |
Step 3. Monitor malware behavior
Here is the dynamic approach to malware analysis. Upload a malware sample to a secure virtual environment. Interact directly with the malware to make the program act and observe its execution. Monitor network traffic, file modifications, and registry changes. And any other suspicious events.
In our online sandbox sample, we can take a look inside the network broadcast to get the rogue’s credential information on C2 and the information that was stolen from an infected machine.
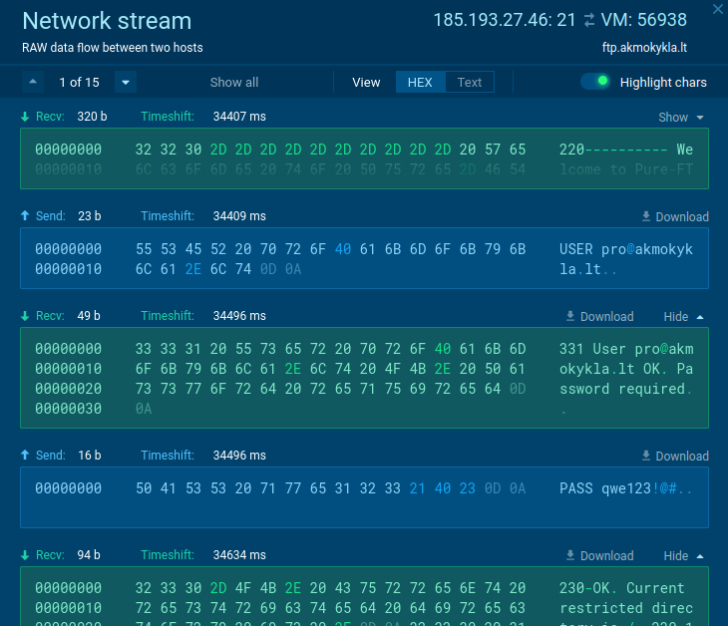 |
| The attacker’s credentials |
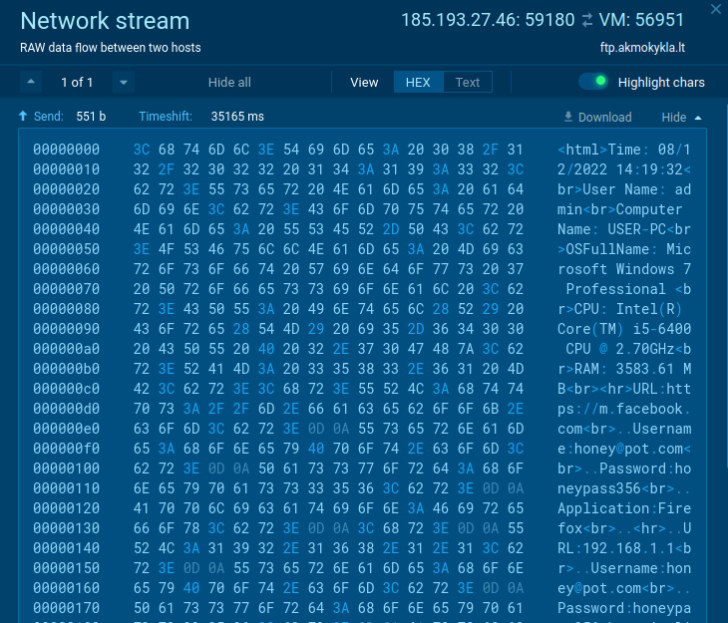 |
| Review of stolen data |
Step 4. Decode
If threat actors obfuscated or packaged the code, use defusion techniques and reverse engineering to uncover the code. Identify skills that were not exposed during the previous steps. Even just looking for a function used by malware can tell you a lot about its functionality. For example, the “InternetOpenUrlA” function says that this malware will make a connection to an external server.
Additional tools, such as debuggers and disassemblers, are required at this stage.
Step 5. Write a malware report.
Include all the findings and data you discovered. Provide the following information:
- Summary of your search with the name, origin and main features of the malware.
- General information about malware type, file name, size, hashes and antivirus detection capabilities.
- Description of malicious behavior, infection algorithm, propagation techniques, data collection and communication methods S2.
- Bitness required OS, software, executable and initializer files, DLL, IP address and scripts.
- Reviewing behavioral activities such as from where it steals credentials, if it modifies, releases or installs files, reads values and checks the language.
- Code analysis results, header data.
- Screenshots, logs, string lines, snippets, etc.
- IOCs.
Interactive malware analysis
Modern antiviruses and firewalls could not manage unknown threats such as targeted attacks, zero-day vulnerabilities, advanced malware and risks with unknown signatures. All these challenges can be solved from an interactive sandbox.
Interactivity is the main advantage of our service. With ANY.RUN you can work directly with a suspicious sample as if you had opened it on your personal computer: click, run, print, reboot. You can work with delayed execution of malware and process different scenarios to get effective results.
During your investigation, you may:
- Get interactive access: work with the VM as on your personal computer: use the mouse, enter data, reboot the system and open files.
- Change the settings: pre-installed softset, several OS with different bitness and builds are ready for you.
- Select tools for your VM: FakeNet, MITM proxies, Tor, OpenVPN.
- Explore network connections: intercept packets and get a list of IP addresses.
- Instant access to analysis: VM immediately starts the analysis process.
- Monitor system processes: observe malware behavior in real time.
- Collect the IOC: IP addresses, domain names, hashes and more are available.
- Get the MITER ATT@CK matrix: review the TTP in detail.
- Have a process chart: evaluate all processes in a graph.
- Download a ready-made malware report: print all data in a suitable format.
All these features help to detect sophisticated malware and see the anatomy of the attack in real time.
Enter the promo code “HACKERNEWS” in the subject of the email to [email protected] and get 14 days premium subscription to ANY.RUN for free!
Try to attack malware using an interactive approach. If you use the ANY.RUN sandbox, you can perform malware analysis and enjoy fast results, a simple search process, investigate even sophisticated malware and get detailed reports. Follow the steps, use smart tools and successfully hunt malware.



