More details have emerged about the operators behind the first known phishing campaign specifically targeting the Python Package Index (PyPI), the official third-party software repository for the programming language.
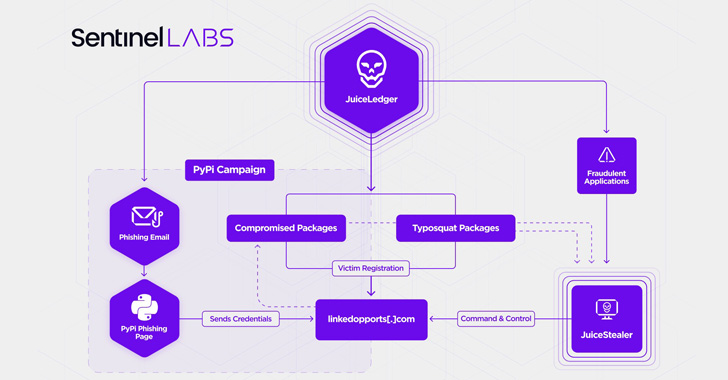
Linking it to a threat actor tracked as JuiceLedgercybersecurity firm SentinelOne, along with Checkmarx, describes the group as a relatively new entity that emerged in early 2022.
The initial “low-key” campaigns reportedly involved using rogue Python installer applications to deliver a .NET-based malware called JuiceStealer that was designed to extract passwords and other sensitive data from victims’ web browsers.

The attacks took a significant turn last month when JuiceLedger actors targeted PyPi package contributors in a phishing campaign, resulting in the compromise of three malware packages.
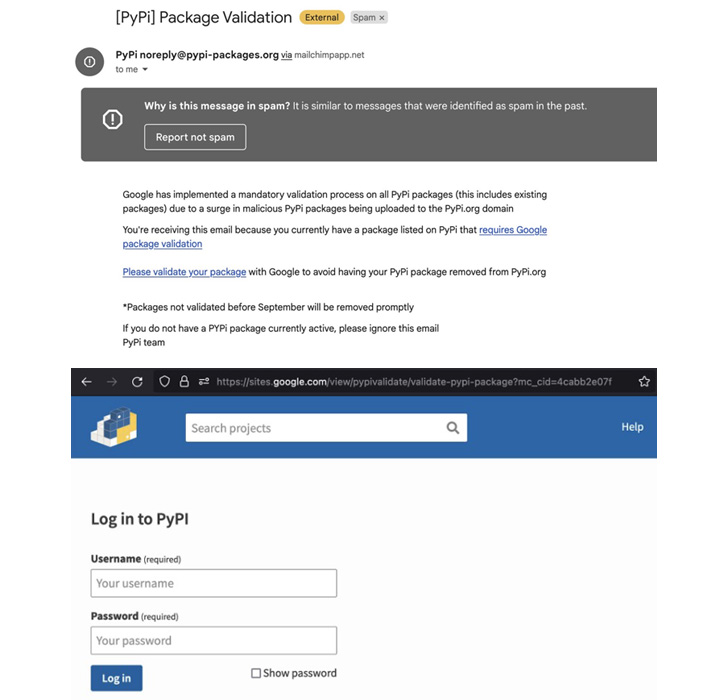
“The supply chain attack on PyPI package contributors appears to be an escalation of a campaign that began earlier this year, which initially targeted potential victims through fake cryptocurrency trading applications,” SentinelOne researcher said in a report , Amitai Ben Shushan Ehrlich.
The aim is apparently to infect a wider audience with the information stealer through a mix of trojanized and typosquat packages, the cyber security firm added.

The development adds to growing concerns about the security of the open source ecosystem, prompting Google to take steps to announce monetary rewards for finding flaws in its projects available in the public domain.
With account takeover attacks becoming a popular infection vector for attackers looking to poison software supply chains, PyPI has begun imposing a mandatory two-factor authentication (2FA) requirement for projects deemed “critical.”
“JuiceLedger appears to have evolved very quickly from small-scale, opportunistic infections just a few months ago to conducting a supply chain attack against a major software distributor,” SentinelOne said.



