
The prolific North Korean nation-state actor known as the Lazarus Group has been linked to a new remote access Trojan called RATI Magic.
The previously unknown piece of malware was said to have been deployed to victims’ networks that were initially breached through successful exploitation of Internet-facing VMware Horizon servers, Cisco Talos said in a report shared with The Hacker News.
“While it is a relatively simple RAT capability from a RAT capability standpoint, it was built using the Qt framework, with the sole purpose of making human analysis more difficult and automated detection through machine learning and heuristics less likely, ” Talos researchers Jung soo An, Asheer. Malhotra, and Vitor Ventura said.

The Lazarus Group, also known as APT38, Dark Seoul, Hidden Cobra and Zinc, refers to a group of financially motivated cyber and espionage activities undertaken by the North Korean government as a means to circumvent sanctions imposed on the country and to fulfill his strategy. the objectives.
Like other umbrella groups Winnti and MuddyWater, the state-sponsored hacking collective also has “spin-off” groups like Bluenoroff and Andariel, which focus on specific types of attacks and targets.
While the Bluenoroff sub-group is focused on attacking foreign financial institutions and committing monetary theft, Andariel is dedicated to going after South Korean organizations and businesses.
“Lazarus develops its own attack tools and malware, can use innovative attack techniques, works very methodically and takes its time,” cybersecurity firm NCC Group said in a report detailing the threat actor.
“In particular, North Korea’s methods aim to avoid detection by security products and remain undetected within hacked systems for as long as possible.”
The latest addition to its extensive suite of malware tools demonstrates the group’s ability to employ a multitude of tactics and techniques depending on their targets and their operational goals.
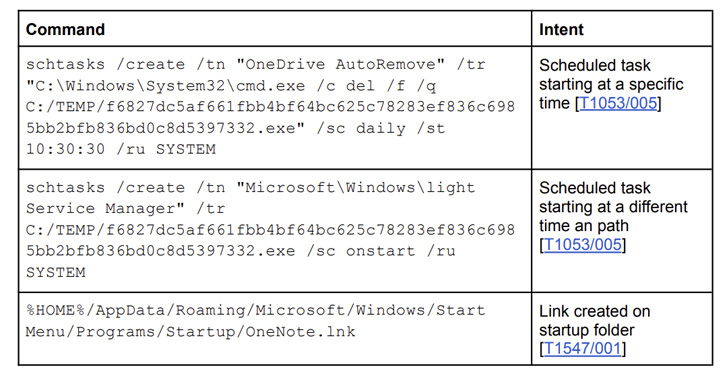
A C++-based implant, MagicRAT is designed to achieve resilience by creating scheduled tasks on the compromised system. It is also “very simple” in that it provides the attacker with a remote shell to run arbitrary commands and perform file operations.

MagicRAT is also capable of dropping payloads received from a remote server on infected hosts. One of the executables received from the command and control server (C2) takes the form of a GIF image file, but is in reality a lightweight port scanner.
Additionally, the C2 infrastructure associated with MagicRAT has been found to host and serve newer versions of TigerRAT, a backdoor previously attributed to Andariel designed to execute commands, capture screenshots, record keyboard and collect system information.
Also included in the latest variant is a USB Dump feature that allows an adversary to search for files with specific extensions, along with laying the groundwork for implementing video capture from webcams.
“The discovery of MagicRAT in the wild is indicative of Lazarus’ motivations to rapidly build new, bespoke malware to be used alongside their previously known TigerRAT malware to target organizations around the world,” the researchers said.



