
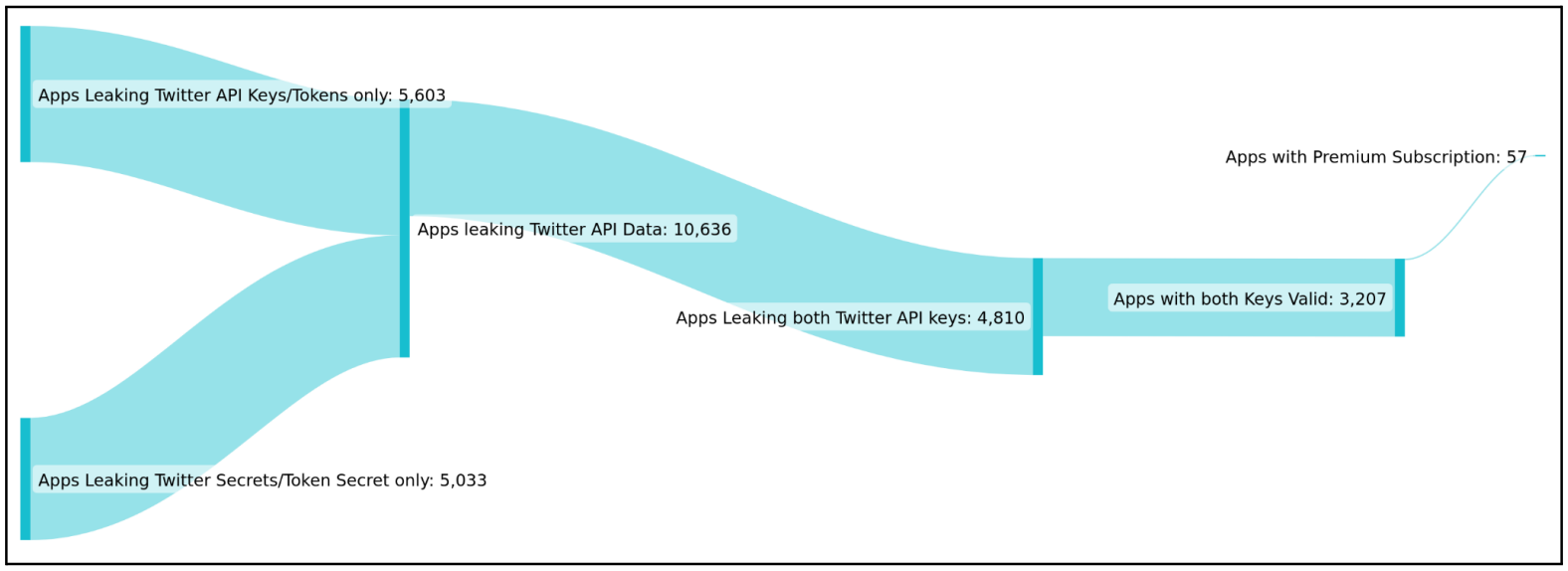
Cybersecurity researchers have discovered a group of 3,207 mobile apps that are exposing Twitter API keys to the public, potentially enabling a threat actor to take over the Twitter accounts of users connected to the app.
The discovery comes from cybersecurity firm CloudSEK, which reviewed large sets of apps for potential data leaks and found 3,207 that exposed a valid customer key and customer secret for Twitter’s API.
When mobile apps integrate with Twitter, developers will be given special authentication keys, or tokens, that allow their mobile apps to interact with Twitter’s API. When a user connects their Twitter account to this mobile application, the keys will also enable the application to act on the user’s behalf, such as registering them via Twitter, creating tweets, sending DMs, etc.
Because access to these authentication keys can allow anyone to perform actions as a connected Twitter user, it is never recommended to store the keys directly in a mobile application where threat actors can find them.
Building an army on Twitter
CloudSEK explains that API key leaks are usually the result of errors by app developers who enter their authentication keys into Twitter’s API but forget to remove them when the mobile is released.
In these cases, an intruder exploiting the flaw could perform the following actions:
- Read direct messages
- Get retweets and likes
- Create or delete tweets
- Remove or add new followers
- Access your account settings
- Changing the screen image
One of the most prominent scenarios for abusing this access, according to CloudSEK, would be for a threat actor to use these exposed tokens to create a Twitter army of verified (trusted) accounts with a large number of followers to promoted fake news, malware campaigns. , cryptocurrency scams, etc.
Bad practices
CloudSEK explains that API key leaks are usually the result of errors by app developers who enter their authentication keys into Twitter’s API but forget to remove them when the mobile is released.
In these cases, credentials are stored within the mobile applications in the following locations:
- resources/res/values/strings.xml
- source/resources/res/values-es-rAR/strings.xml
- source/resources/res/values-es-rCO/strings.xml
- source/sources/com/app-name/BuildConfig.java
CloudSEK recommends that developers use API key rotation to protect authentication keys, which would invalidate exposed keys after a few months.
Who is affected?
CloudSEK shared a list of affected apps with BleepingComputer, with apps between 50,000 and 5,000,000 downloads, including city transport companions, radio tuners, book readers, event recorders, newspapers, e-banking apps, GPS apps for cycling and more.
Most apps that publicly expose their API keys haven’t even acknowledged receiving CloudSEK’s notices a month after the cybersecurity firm alerted them, and most haven’t addressed the issues.
As such, BleepingComputer will not reveal the list of apps as they are still vulnerable to Twitter exploits and account takeovers.
One notable exception was Ford Motors, which responded and deployed a fix to the ‘Ford Events’ app that was also leaking Twitter API keys.



