
An ongoing espionage campaign operated by the Russian-linked Gamaredon group is targeting employees of Ukrainian government, defense and law enforcement agencies with a piece of custom-made information-stealing malware.
“The adversary is using phishing documents that contain lures related to the Russian invasion of Ukraine,” Cisco Talos researchers Asheer Malhotra and Guilherme Venere said in a technical write-up shared with The Hacker News. “LNK, PowerShell, and VBScript files enable initial entry, while malicious binaries are deployed in the post-infection phase.”
Active since 2013, Gamaredon – also known as Actinium, Armageddon, Primitive Bear, Shuckworm and Trident Ursa – has been linked to multiple attacks targeting Ukrainian entities following the Russian military invasion of Ukraine in late February 2022.

The targeted phishing operation, traced back to August 2022, also follows similar intrusions discovered by Symantec last month involving the use of malware such as Giddome and Pterodo. The main purpose of these attacks is to create long-term access for espionage and data theft.
It involves exploiting Microsoft Word documents containing decoys related to the Russian-Ukrainian war that are distributed via e-mail messages to infect targets. When opened, macros hidden within the remote templates are executed to retrieve RAR files containing LNKs.
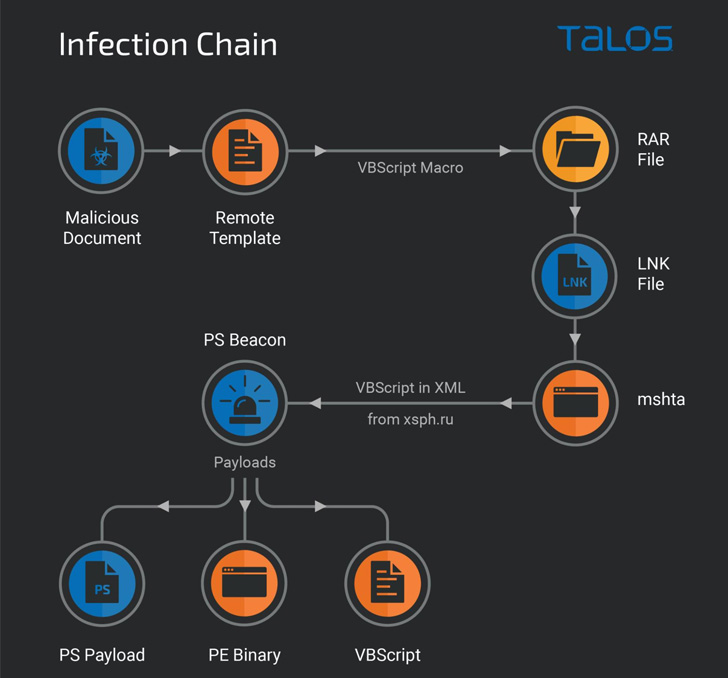
The LNK files apparently refer to intelligence information about the Russian invasion of Ukraine to trick unsuspecting victims into opening shortcuts, resulting in the execution of a PowerShell script that eventually paves the way for stage payloads other.
This includes another PowerShell script used to provide persistent access to the compromised system and deliver additional malware, including a new malware capable of hijacking files (.doc, .docx, .xls, .rtf , .odt, .txt, .jpg, .jpeg, .pdf, .ps1, .rar, .zip, .7z and .mdb) from the device as well as any removable drives connected to it.

“Infostealer is a dual-purpose malware that includes capabilities to exfiltrate specific file types and place additional binary and script-based payloads on an infected endpoint,” the researchers said, adding that it may be a component of the Giddome family backdoor.
The revelations come at a time when cyber attacks continue to be an important part of the modern hybrid warfare strategy amid the conflict between Russia and Ukraine. Earlier this month, Google’s Threat Analysis Group (TAG) discovered up to five different campaigns mounted by a group with links to the Conti cybercrime cartel.



