
As threat complexity increases and an organization’s boundaries disappear, security teams are more challenged than ever to deliver consistent security results. One company that aims to help security teams meet this challenge is Stellar Cyber.
Stellar Cyber claims to address the needs of MSSPs by offering capabilities typically found in NG-SIEM, NDR, and SOAR products on their Open XDR platform, managed with a single license. According to Stellar Cyber, this consolidation means faster security analyst turnaround time and customer onboarding with far less intensive manual tasks required. Stellar Cyber currently counts 20+ of the leading MSSP providers as clients, providing security for over 3 million assets. In addition, Cyber Star claims after deployment, users see up to 20x faster mean time to respond (MTTR), a bold claim.
We recently took a closer look at the Stellar Cyber Security Operations Platform.
Before we start
Before digging into the platform, here are a few things MSSPs should know about Stellar Cyber:
- Works with any EDR: Stellar Cyber can be classified as an open XDR as it provides visibility into your customer’s environments; however, it is not an extension of an EDR product. In contrast, Stellar Cyber offers pre-built integrations for every major EDR vendor which means your customers can use whatever EDR they want if you use Stellar Cyber.
- It is multi-tenanted: Stellar Cyber is a multi-tenant solution that means your customer’s data won’t be mixed up, enabling you to offer your services in regions that are particularly concerned about data privacy. Further, this multi-tenant approach can drive better analyst-to-client ratios. In certain situations, work done for one client can be applied to another with zero loss of data integrity.
To facilitate this product review, the team at Stellar Cyber gave us access to the cloud-based version of their product, so after a brief description of the product provided by a Stellar Cyber support person, we were we locked in the product.
Responding to an incident from the home page
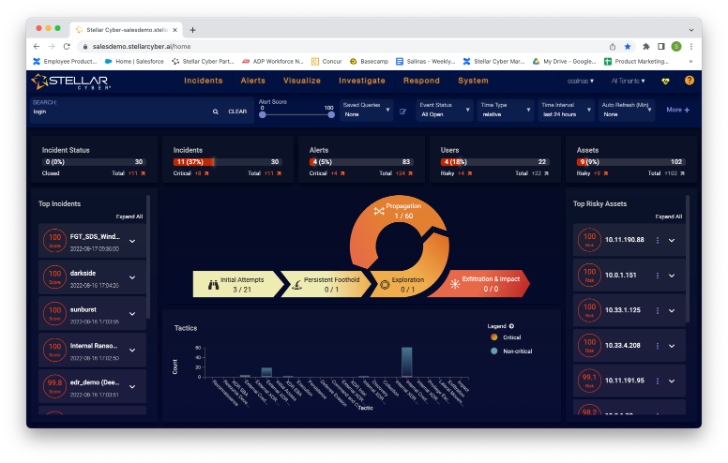
This is the splash screen you see when you log into Stellar Cyber. You can expect to see many elements on the analyst’s home screen, such as top incidents and riskiest assets. An interesting piece on this display is what Stellar Cyber calls the Open XDR Kill Chain. By clicking on each segment of the kill chain, you can access the threats associated with that part of the attack chain. For example, I clicked on Initial Attempts to access this screen.
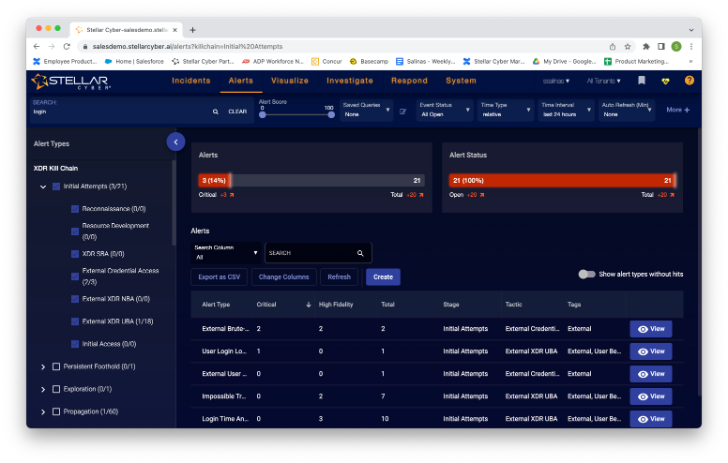
Here I can see these alerts with the “Initial Attempts” stage set by Stellar Cyber automatically. Further down the rabbit hole, I see more information about the alert when I click “View” on any of the alerts. First, I was presented with some summary graphs, then scrolling down the screen a bit, I saw a “more info” hyperlink, so I clicked on it and got this in return.
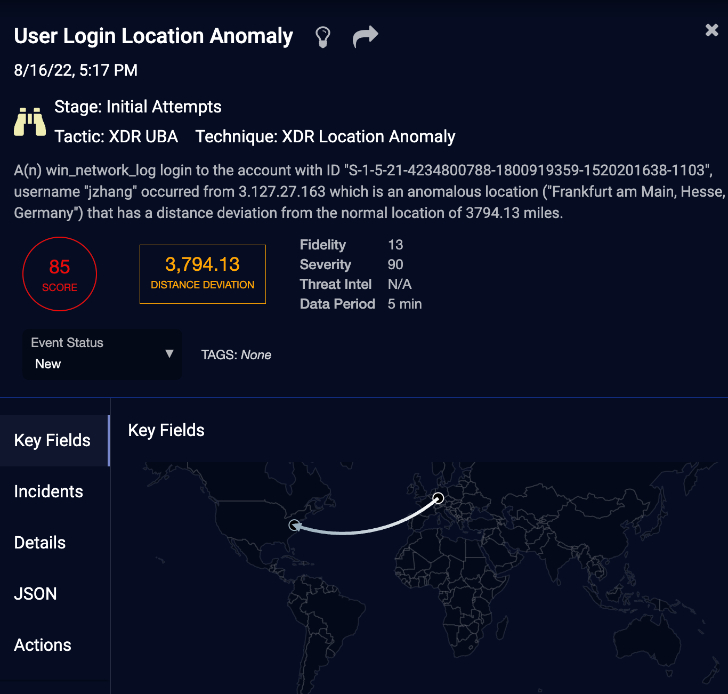
Here I can read about the incident, drill down into the details, and review the raw data behind this incident, as well as the JSON, which I can easily copy to a console if needed.
This is where I thought things got a little more interesting. While the presentation of data in Stellar Cyber is easy to understand and logical, the true power of the product was not apparent to me until I clicked on the Actions button on the screen above.
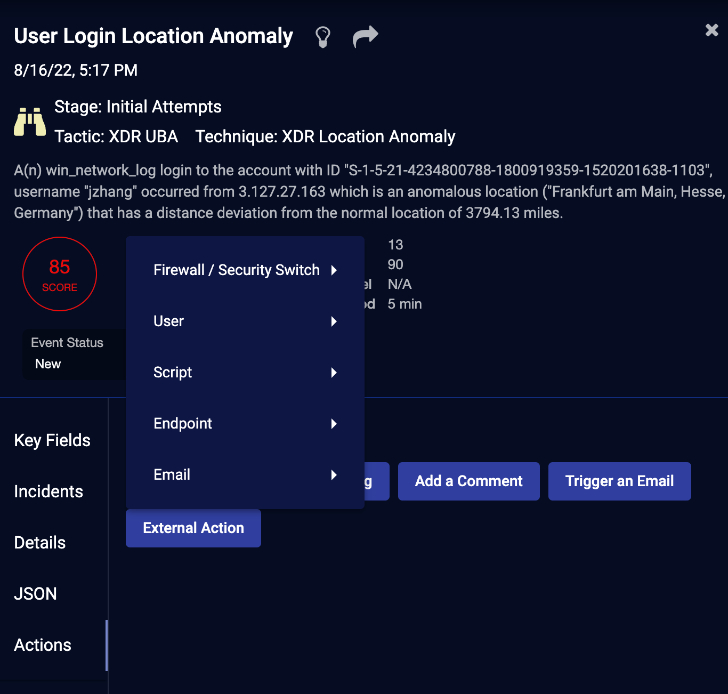
As you can see, I can perform my response actions directly from this screen, such as “add a filter, trigger an email, or perform an external action. By clicking on the external action, I get another list of choices. When I click on Endpoint, I get a long list of options from host contains to shutdown host.
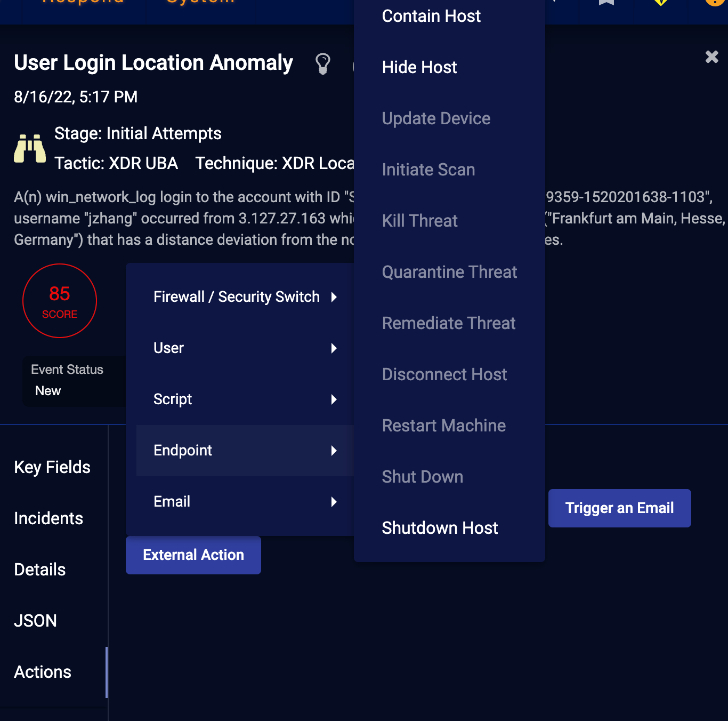
When you click an action, such as contains host, a configuration dialog appears where I can select the connector to use, the target of the action, and any other options required to launch the selected action. So, in summary, I can see how security analysts, especially new ones, will find this workflow very useful in that they can a) easily drill down into the details of an incident from the home screen, b) examine even more details by drilling down into the data and c) take a corrective action from this screen without writing any script or changing any code.
For MSSPs, I could see new analysts being brought on board to work on this view first to familiarize them with the platform while helping to meet customer service level agreements. However, my gut tells me that there is much more to learn about this Stellar Cyber platform, so let’s see if there is another way to investigate the incidents.
Incident Exploration
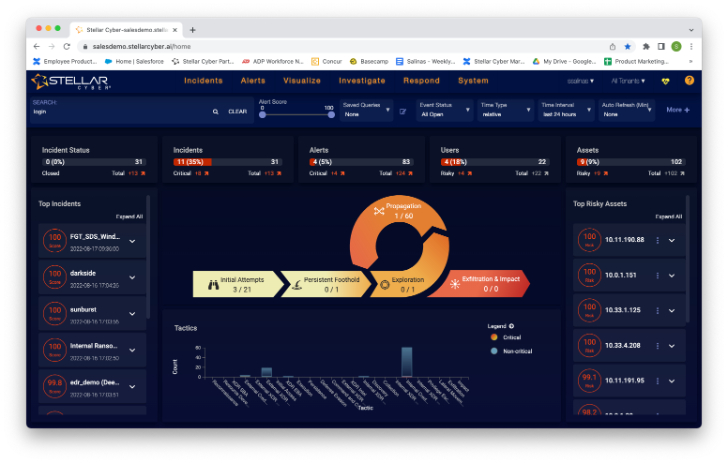
Now instead of clicking on Open XDR Kill Chain, I’ll click on the Incidents menu item and get this screen instead.
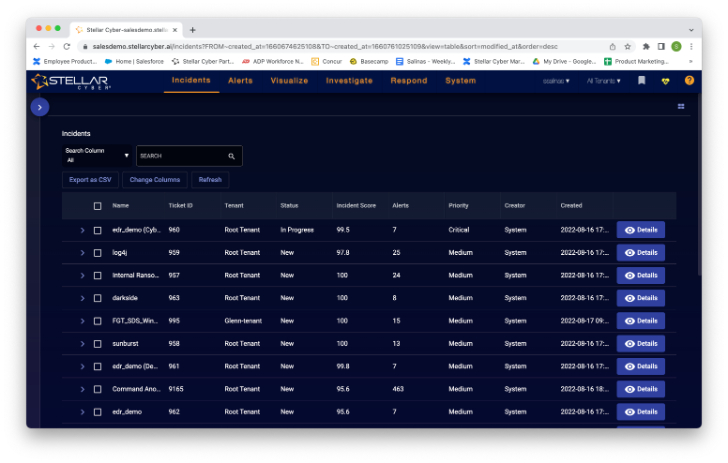
When I clicked on the carrot in the blue circle, it expanded a filter list that allowed me to drill down to a specific type of incident. Since I’m in exploratory mode, I go straight to the details button to see what I can find in this detailed view.
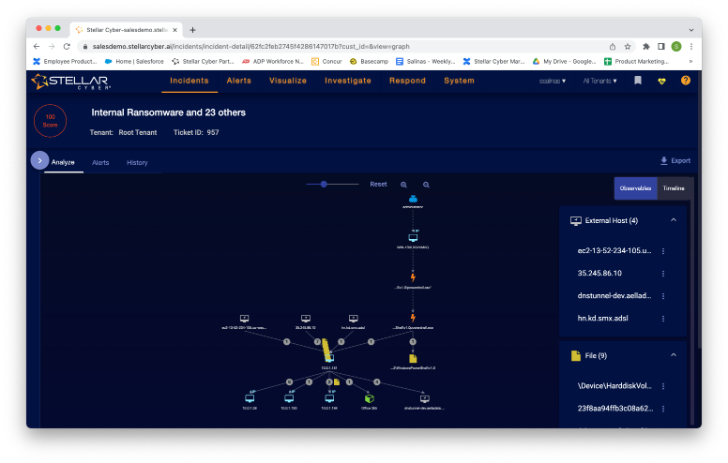
Now I can see how this incident happened and spread across multiple assets. Further, I can automatically see the files, processes, users and services associated with the incident. There are different ways to view this data as well. For example, I can switch to the timeline view to get a readable history of this incident, like this:
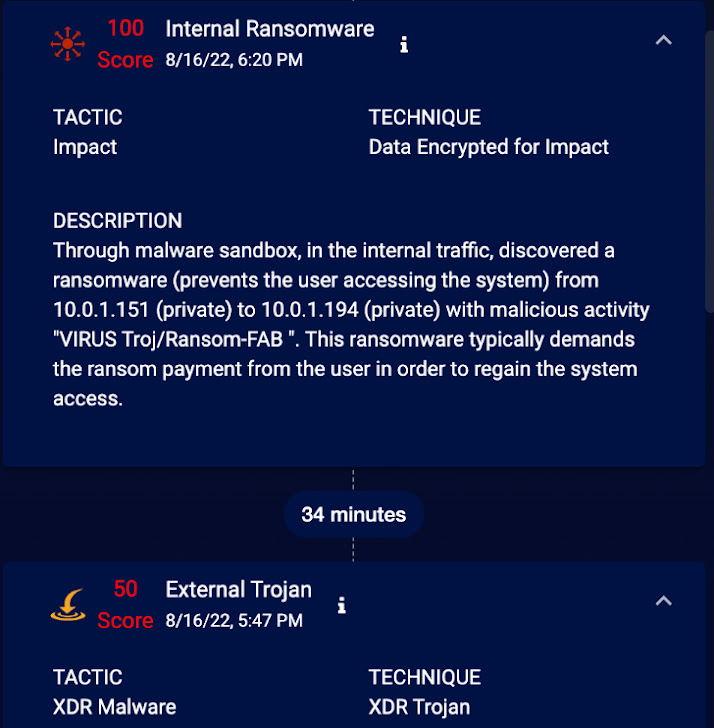
When I click on the little “i” I go to a familiar screen.
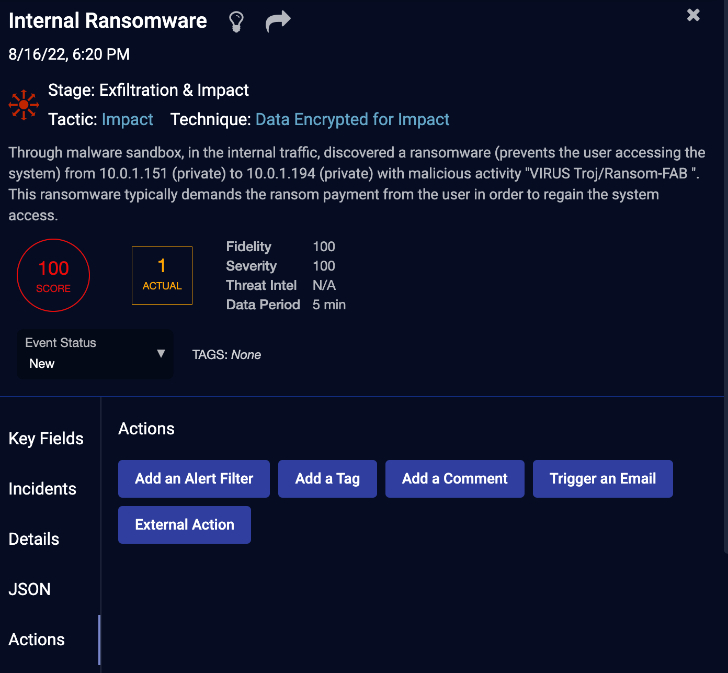
I know the story from here, which is good.
So, in summary, I can see that analysts who are used to working from a list of alerts may want to start their investigations from the incidents page. For MSSPs, this view is also useful as it shows all incidents across all tenants in a single view. Of course, you can limit this view to analysts, customers, etc.
Threat hunting and response actions at Stellar Cyber
Until then, I am convinced that Stellar Cyber offers an interesting approach for MSSPs looking to streamline their security operations. Honestly, at this point in my review, I haven’t had to write any special scripts or do anything other than click a few links and scroll through a few screens to hypothetically respond to some bad alerts, which I don’t. is the norm for these types of products.
Before I sing Stellar Cyber’s praises too much, I wanted to take a look at a few other stated features, Threat Hunting and Response Actions (aka SOAR). Let’s start with threat hunting. When I click “Threat Hunting” from the menu, I get this screen.
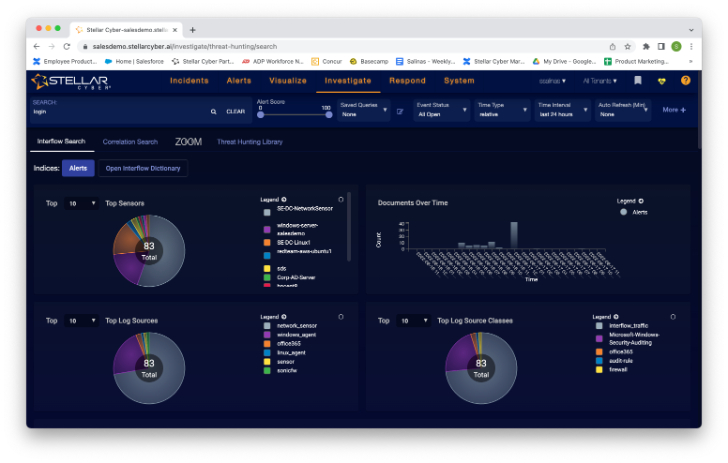
While these stats are interesting, I’m looking for h-threat; here I see the search dialog box on the top right. I write the entry and notice that the statistics change dynamically. Scrolling down the screen, I also see a list of alerts that have been filtered based on my search term. Here I see the familiar “more info” option, so I know where it will take me.
I also noticed something called “correlation search” under the search dialog box. When I click that, my screen changes to this.
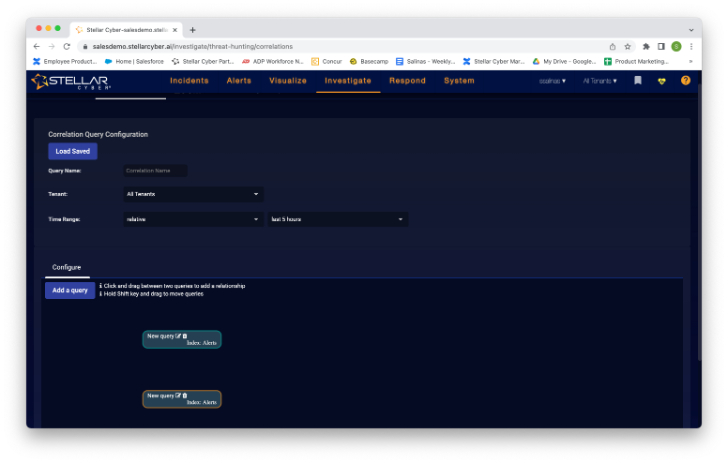
I can load a saved question or add a new question. Clicking the add question, I see this question builder. This allows me to search basically any data in the Stellar Cyber stores to theoretically find threats that went unnoticed. I can also access the threat hunting library to access previously saved queries.
You can also create response actions that will be executed automatically if the query you create returns any matches.
So in summary, Stellar Cyber offers a simple threat hunting platform that doesn’t require you to build your own ELK stack or be a power scripter. For MSSPs, I can see this being a good value add that they can provide to customers when emerging threats are detected in nature.
Conclusion
Stellar Cyber is a solid security operations platform with many features for the MSSP user. If you’re in the market for a new SecOps platform, it’s worth taking a look at what Stellar Cyber has to offer.



